💡 Risk Management in Technology
Risk management is the process of identifying, assessing, and prioritising and implementing strategies to mitigate or transfer risks. It is a continuous process that involves ongoing monitoring and reassessment of risks and the effectiveness of the strategies selected.
When it comes to technology, risk management is a crucial activity for addressing various challenges and ensuring the smooth operation of IT systems. Effective risk management practices play a vital role in mitigating cybersecurity threats by identifying vulnerabilities, implementing security controls, and responding promptly to incidents. This proactive approach helps organisations safeguard their digital assets, protect sensitive data, and prevent unauthorised access or data breaches.
Additionally, risk management strategies help minimise the risk of system outages by identifying potential points of failure, implementing redundancy measures, and establishing robust disaster recovery plans. By addressing vulnerabilities and ensuring system resilience, organisations can reduce downtime, maintain operational continuity, and minimise disruptions to business operations.
An essential aspect of effective risk management is its ability to build trust with stakeholders, customers, and partners by demonstrating a commitment to security, reliability, and compliance. Proactively managing risks and protecting sensitive information enhances an organisation's reputation, instils confidence, and fosters long-term relationships based on trust and transparency.
Furthermore, risk management ensures compliance with legal and regulatory standards, such as the General Data Protection Regulation (GDPR), Payment Card Industry Data Security Standard (PCI DSS), or Australian Prudential Regulation Authority (APRA) CPS 234. Aligning risk management practices with industry regulations enables organisations to avoid penalties, protect customer data, and uphold ethical standards in technology operations.
Risk Management in Action
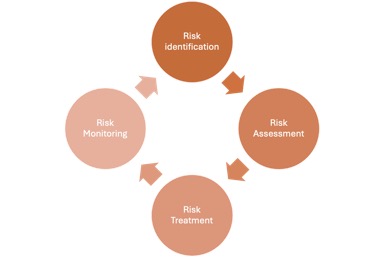
The risk management process is usually comprised of 4 steps:- Risk identification: identify potential threats and vulnerabilities.
- Risk assessment: estimate impact and likelihood of a risk.
- Risk treatment: decide on the appropriate risk response.
- Risk monitoring: evaluate the identified risks and ensure the effectiveness of the risk treatment.
Risk Identification
To manage risk, the first step is to identify potential threats and vulnerabilities. In the context of technology risk and cybersecurity, threat actors are individuals or groups who seek to exploit vulnerabilities in an organisation's information system for personal gain or malicious intent. Threat actors can come from a variety of sources:- Insiders can be a significant threat, as they have access to sensitive information and may have malicious intent, act through simple human error, or due to gross incompetence. For example, an employee who intentionally accesses and shares sensitive data with unauthorised individuals can compromise an organisation's confidentiality.
- Outside individuals or informal groups can be opportunistic or planned attackers, who may discover vulnerabilities through various means, including social engineering or technical exploits. They may be motivated by financial gain or other malicious intentions.
- Formal entities that are non-political, such as business competitors and cybercriminals, may also pose a significant threat to an organisation's information security. These attackers may use sophisticated techniques and tools to exploit vulnerabilities, and their motives may include financial gain or other objectives.
- Formal entities that are political, such as terrorists, nation-states, and hactivists, may use cyberattacks to achieve their political goals or disrupt an organisation's operations.
- Intelligence or information gatherers, who may be any of the above, also pose a significant threat to organisations. They may use various techniques to gather sensitive information, including social engineering or technical exploits.
- Finally, technology itself, such as free-running bots and artificial intelligence, can be part of any of the above categories and may pose a significant threat to an organisation's information security.
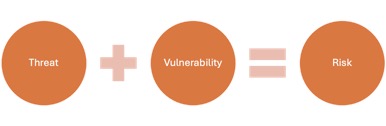
Vulnerabilities are weaknesses in a system that a treat might exploit to undermine the confidentiality, integrity or availability of the organisation. Vulnerabilities might include missing patches or misconfiguration.
Risks occur when an environment contains both a vulnerability and a corresponding threat that might exploit that vulnerability. For example, if a company forget to update their antivirus signatures on their workstations and hackers release a new virus upon the internet, the organisation faces a risk. It is vulnerable because it is missing a security control, and there is a threat: the new virus.
Risk Assessment
Once risks have been identified, the next step is to assess them. This involves estimating and prioritising risks to an organisation’s operations (including its mission, functions, image, and reputation), assets, individuals, and other organisations (even the nation). The risk assessment process should result in aligning (or associating) each identified risk resulting from the operation of an information system with the goals, objectives, assets, or processes of the organisation.One common method for prioritising risks is the likelihood (or probability) and impact model. This model involves assessing the likelihood of a risk occurring and the potential impact if it does occur. For example, a hospital might identify the risk of a cyberattack on its patient data. The hospital might estimate that the likelihood of a successful attack is high, and that the impact would be severe. Based on this assessment, the hospital might prioritise this risk as a high priority and take steps to mitigate it.
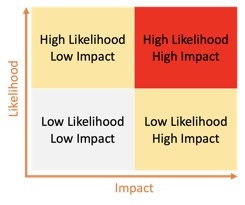
A tool used for such assessment is a risk prioritisation matrix. It helps organisations determine which risks to prioritise for action based on their likelihood and potential impact. The matrix typically divides risks into three categories: high priority, medium priority, and low priority. For example, a bank might use a risk prioritisation matrix to determine that a phishing attack on its customers is a high priority risk, while a minor software vulnerability is a low priority risk.
Risk Treatment
After risks have been identified, assessed, and prioritised, organisations can decide on appropriate risk response strategies. These strategies might include:- Accept the risk: Risk acceptance (sometime also called risk tolerance) is taking no action to reduce the likelihood of a risk occurring. For example, a small business might accept the risk of a data breach because the cost of implementing additional security measures is too high.
- Avoid the risk: Risk avoidance is the decision to attempt to eliminate the risk entirely. For example, a company might avoid the risk of a cyberattack by discontinuing the use of a particular software program that is known to have vulnerabilities.
- Mitigate (i.e. reduce) the risk: Risk mitigation is the most common type of risk management and includes taking actions to prevent or reduce the possibility of a risk event or its impact. For example, a company might mitigate the risk of a data breach by implementing two-factor authentication for all user accounts.
- Transfer or share the risk: Risk transference is the practice of passing the risk to another party, who will accept the financial impact of the harm resulting from a risk being realised in exchange for payment. For example, an insurance company might offer cybersecurity insurance to a business, transferring the risk of a cyberattack to the insurance company.
Risk MonitoringRisk monitoring is essential for ongoing evaluation and surveillance of identified risks to ensure the effectiveness of risk management strategies. The key components of risk monitoring are:
- Regular Reassessment: periodic reviews of risks are crucial to adapt to changing threats and vulnerabilities. Regular reassessments help identify new risks, evaluate existing controls, and adjust strategies accordingly.
- Performance Metrics and Reporting: Establishing indicators and reporting mechanisms is vital for tracking risk management effectiveness and communicating risk-related information to stakeholders. Various stakeholders will have different expectations when it comes to metrics and reporting. Senior management will usually focus on Key Risk Indicators (KRIs), used to monitor and assess the likelihood of potential risks, and Key Performance Indicators (KPIs), used to measure the performance of an organisation in achieving its objectives. Operational management will usually focus more on Key Control Indicators (KCIs), used to evaluate the effectiveness of controls in place to mitigate risks.
- Assurance: Assurance activities validate risk management processes:
- Self-Assessment and Internal evaluations help identify gaps, assess compliance, and drive improvement in risk management practices.
- Simulated exercises evaluate security controls and incident response procedures to identify weaknesses and enhance security posture.
- Independent reviews and audits assess risk management processes, controls, and compliance to ensure accountability and transparency.
Managing information security risks requires a systematic approach that includes identifying and assessing risks, prioritising risks based on their probability and impact, selecting appropriate risk response strategies, and ongoing monitoring of the risk. By following these steps, organisations reduce the likelihood and impact of security incidents and protect their valuable assets, reputation, and customers.
The Risk Management Process enables organisations to assess and prioritise risks and decide on appropriate risk response strategies. Organisations should have a systematic approach to identifying risks, assessing their potential impact, and deciding on appropriate risk response strategies.
Controls
In order to mitigate risks related to technology, organisations put in place measures to safeguard their systems and data. These measures are called controls.Controls in information security can be broadly categorised into three main types based on their functions: preventive, detective, and corrective measures. These categories help organisations establish a comprehensive approach to managing risks and enhancing the security of their systems and data.
- Preventive controls are proactive measures designed to stop security incidents before they occur. These controls aim to prevent unauthorised access, data breaches, and other security threats. Examples of preventive controls include implementing strong password policies, conducting regular security training for employees, and deploying firewalls to block malicious traffic.
- Detective controls are mechanisms put in place to identify security incidents that have already occurred. These controls help organisations detect anomalies, unauthorised access, or other security breaches in a timely manner. Examples of detective controls include security monitoring tools, intrusion detection systems, and log analysis to track and investigate suspicious activities.
- Corrective controls are reactive measures taken in response to security incidents to minimise their impact and prevent future occurrences. These controls focus on remediation and recovery after a security breach has been identified. Examples of corrective controls include incident response plans, data recovery procedures, and system patches to address vulnerabilities exploited during an attack.
By understanding and implementing a combination of preventive, detective, and corrective controls, organisations can establish a robust security posture that effectively mitigates risks and safeguards their information systems and data.
Quantitative Risk Model
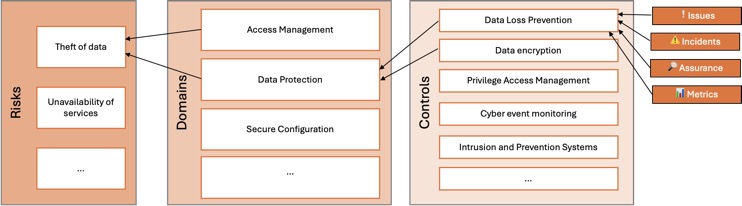
A quantitative risk model provides organisations with a structured framework to assess and manage risks using numerical data and metrics. In this model, controls are meticulously evaluated and scored based on a combination of factors, including monitoring metrics (Key Control Indicators - KCIs), outcomes of assurance and testing activities, and the frequency of known issues and incidents. This data-driven approach allows organisations to gain a deeper understanding of control effectiveness and make informed decisions to mitigate risks effectively.Controls within the quantitative risk model are categorised into technology domains, each representing a critical aspect of technology capabilities. These domains are designed to work in harmony, with controls within each of them complementing one another. If one control proves to be less effective, another control within the same domain can compensate for any deficiencies. Furthermore, controls are weighted based on their significance in supporting the domains. By assigning weights to controls, organisations can determine the overall maturity level of each domain based on the collective ratings of its constituent controls.
For instance, when assessing the risk of data being exfiltrated, organisations may focus on various domains such as "secure configuration," "access management," and "data protection." Within each of these domains, there are multiple weighted controls, such as "data loss prevention," "data classification," and "encryption." By evaluating these domains and their respective controls, organisations can develop a comprehensive understanding of control effectiveness and identify areas for improvement.
Organisations can leverage established risk and control models, such as COBIT or NIST 800-37 management frameworks, to enhance their quantitative risk management approach. These frameworks provide guidelines and best practices for implementing effective controls, assessing risks, and improving overall governance in technology environments. By aligning with recognised models, organisations can streamline their risk management processes, enhance control effectiveness, and strengthen their resilience against cybersecurity threats.
By leveraging a quantitative risk model, organisations can systematically analyse and prioritise controls, identify strengths and weaknesses in their risk management approach, and make data-driven decisions to enhance their overall risk posture. This methodical approach empowers organisations to quantify risks more accurately, enhance control effectiveness, and fortify their resilience against evolving threats in the technology and cybersecurity landscape.
Conclusion
In conclusion, effective risk management is a crucial element in ensuring the security, reliability, and compliance of technology operations within organisations. By systematically identifying, assessing, prioritising, and implementing strategies to mitigate risks, organisations can proactively safeguard their digital assets, protect sensitive data, and maintain operational continuity.Moreover, risk management practices not only help organisations address cybersecurity threats and prevent system outages but also enable them to build trust with stakeholders, customers, and partners by demonstrating a commitment to security and compliance. By aligning risk management strategies with industry regulations and standards, organisations can avoid penalties, protect customer data, and uphold ethical standards in their technology operations.
Through the implementation of physical, technical, and administrative controls, organisations can reduce the risk of security incidents and protect their information systems and data. Additionally, leveraging a quantitative risk model provides organisations with a structured framework to assess and manage risks using numerical data and metrics, enabling them to make informed decisions to mitigate risks effectively and strengthen their resilience against evolving cybersecurity threats.
Overall, a comprehensive and systematic approach to risk management not only enhances an organisation's security posture but also contributes to its long-term success by fostering trust, compliance, and resilience in the ever-evolving landscape of technology and cybersecurity.
Disclaimer: This article is not legal or regulatory advice. You should seek independent advice on your legal and regulatory obligations. The views and opinions expressed in this article are solely those of the author. These views and opinions do not necessarily represent those of AMP or its staff. Artificial Intelligence Technology was used to read-proof this article.